divineomega / password_exposed
This PHP package provides a `password_exposed` helper function, that uses the haveibeenpwned.com API to check if a password has been exposed in a data breach.
Fund package maintenance!
DivineOmega
Installs: 1 624 010
Dependents: 5
Suggesters: 0
Security: 0
Stars: 222
Watchers: 6
Forks: 37
Open Issues: 0
pkg:composer/divineomega/password_exposed
Requires
- php: ^7.1||^8.0
- jord-jd/do-file-cache-psr-6: ^3.0
- jord-jd/psr-18-guzzle-adapter: ^3.0
- nyholm/psr7: ^1.0
- paragonie/certainty: ^2.4
- php-http/discovery: ^1.6
- psr/cache: ^1.0 || ^2.0 || ^3.0
- psr/http-client: ^1.0
- psr/http-factory-implementation: ^1.0
- psr/http-message: ^1.0 || ^2.0
- psr/http-message-implementation: ^1.0
Requires (Dev)
- fakerphp/faker: ^1.23
- kriswallsmith/buzz: ^1.0
- phpunit/phpunit: ^9.6
- symfony/cache: ^4.2.12
- vimeo/psalm: ^4
Replaces
- divineomega/password_exposed: v5.0.2
- dev-master / 5.0.x-dev
- v5.0.2
- v5.0.1
- v5.0.0
- v4.0.0
- v3.2.0
- v3.1.1
- v3.1.0
- v3.0.1
- v3.0.0
- v2.8.0
- v2.7.0
- v2.6.0
- v2.5.5
- v2.5.4
- v2.5.3
- v2.5.2
- v2.5.1
- v2.5.0
- v2.4.0
- v2.3.3
- v2.3.2
- v2.3.1
- v2.3.0
- v2.2.0
- v2.1.1
- v2.1.0
- v2.0.0
- v1.0.1
- v1.0.0
- dev-dependabot/composer/php-http/discovery-tw-1.20
- dev-dependabot/github_actions/actions/checkout-6
- dev-dependabot/composer/php-coveralls/php-coveralls-tw-2.9
- dev-dependabot/composer/psr/http-message-tw-2.0
- dev-dependabot/composer/kriswallsmith/buzz-tw-1.3
- dev-dependabot/composer/nyholm/psr7-tw-1.8
This package is auto-updated.
Last update: 2026-02-15 21:46:26 UTC
README
This PHP package provides a password_exposed helper function, that uses the haveibeenpwned.com API to check if a password has been exposed in a data breach.
CI is run via GitHub Actions (unit tests, Psalm, and PHP syntax checks).
Installation
The password_exposed package can be easily installed using Composer. Just run the following command from the root of your project.
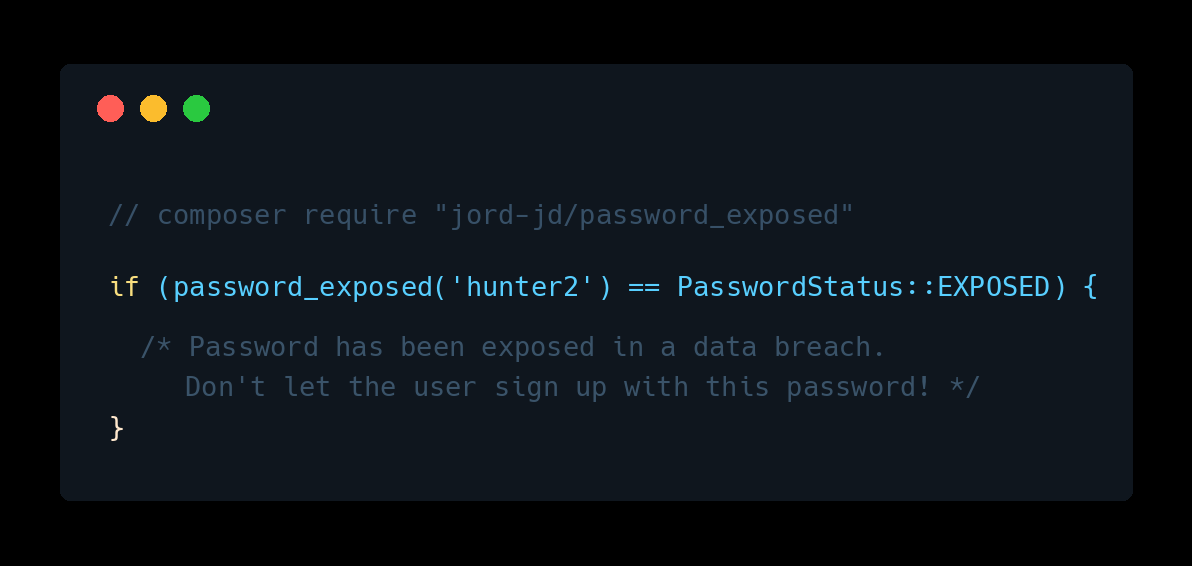
composer require "jord-jd/password_exposed"
If you have never used the Composer dependency manager before, head to the Composer website for more information on how to get started.
Usage
To check if a password has been exposed in a data breach, just pass it to the password_exposed method.
Here is a basic usage example:
switch(password_exposed('hunter2')) { case PasswordStatus::EXPOSED: // Password has been exposed in a data breach. break; case PasswordStatus::NOT_EXPOSED: // Password has not been exposed in a known data breach. break; case PasswordStatus::UNKNOWN: // Unable to check password due to an API error. break; }
If you prefer to avoid using helper functions, the following syntax is also available.
$passwordStatus = (new PasswordExposedChecker())->passwordExposed($password);
SHA1 Hash
You can also supply the SHA1 hash instead of the plain text password, by using the following method.
$passwordStatus = (new PasswordExposedChecker())->passwordExposedByHash($hash);
or...
$passwordStatus = password_exposed_by_hash($hash);