camilord / twofactor_gauthenticator
This RoundCube plugin adds the 2-factor authentication during login. This is a forked from https://github.com/alexandregz/twofactor_gauthenticator
Package info
github.com/camilord/twofactor_gauthenticator
Type:roundcube-plugin
pkg:composer/camilord/twofactor_gauthenticator
Requires
- php: >=5.3.0
- ext-openssl: *
This package is auto-updated.
Last update: 2026-02-11 23:54:20 UTC
README
Requirement
- Roundcube Webmail 1.5.x
Changelog
- fixed UI using bootstrap 4.5.x
- improved UI form functionalities
Features difference from alexandregz/twofactor_gauthenticator
- Remember Device in days can be configured. It was 30 days before, now the default is 7 days. 30 days is too much.
- When you enable the config
force_enrollment_usersto enforce all users to use 2FA, I have added an option to exclude some users/domain enforcing 2FA. - When you click the Activate checkbox, will generate the
secret keyandrecovery codesright away - You can also regenerate the
secret key - QR Code always display
- In testing the codes from you app, will display the server time.
- Settings > 2FA form = fixed to work or display well in Roundcube Webmail v1.5.x
- Cleaner code, better indention, reformat codes using PHPStorm
How to install this plugin?
- download the package and extract the contents
- should have a folder called
twofactor_gauthenticator - move the folder to roundube install destination under
pluginsfolder:{ROUNDCUBE_INSTALL}/plugins/ - then define your configuration, copy
{ROUNDCUBE_INSTALL}/plugins/config.inc.php.distas{ROUNDCUBE_INSTALL}/plugins/config.inc.php - that's it. login to you account, go to config and
2-factor Authenticationoption should appear - activate the 2FA in your account, fill up the form and you're good to go.
NOTES
- before you save the generated secret key, make sure you tested it using the "Test the generated PIN here"
- If you keep getting "incorrect code", meaning your PC time and the server time is not the same.
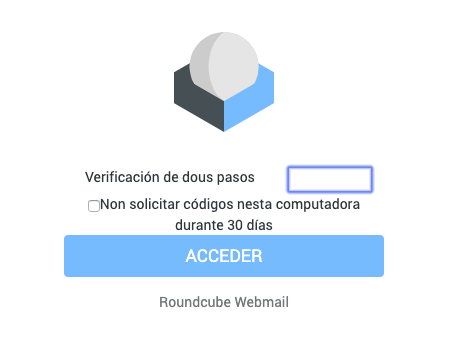
2Steps verification
This RoundCube plugin adds the 2-step verification(OTP) to the login proccess.
It works with all TOTP applications RFC 6238
Some code by: Ricardo Signes Justin Buchanan Ricardo Iván Vieitez Parra
GoogleAuthenticator class by Michael Kliewe (to see secrets)
qrcode.js by ShimSangmin
Also thx to Victor R. Rodriguez Dominguez for some ideas and support
Installation
- Clone from github: HOME_RC/plugins$ git clone https://github.com/alexandregz/twofactor_gauthenticator.git
(Or use composer HOME_RC$ composer require alexandregz/twofactor_gauthenticator:dev-master
NOTE: Answer N when composer ask you about plugin activation)
- Activate the plugin into HOME_RC/config/config.inc.php: $config['plugins'] = array('twofactor_gauthenticator');
Configuration
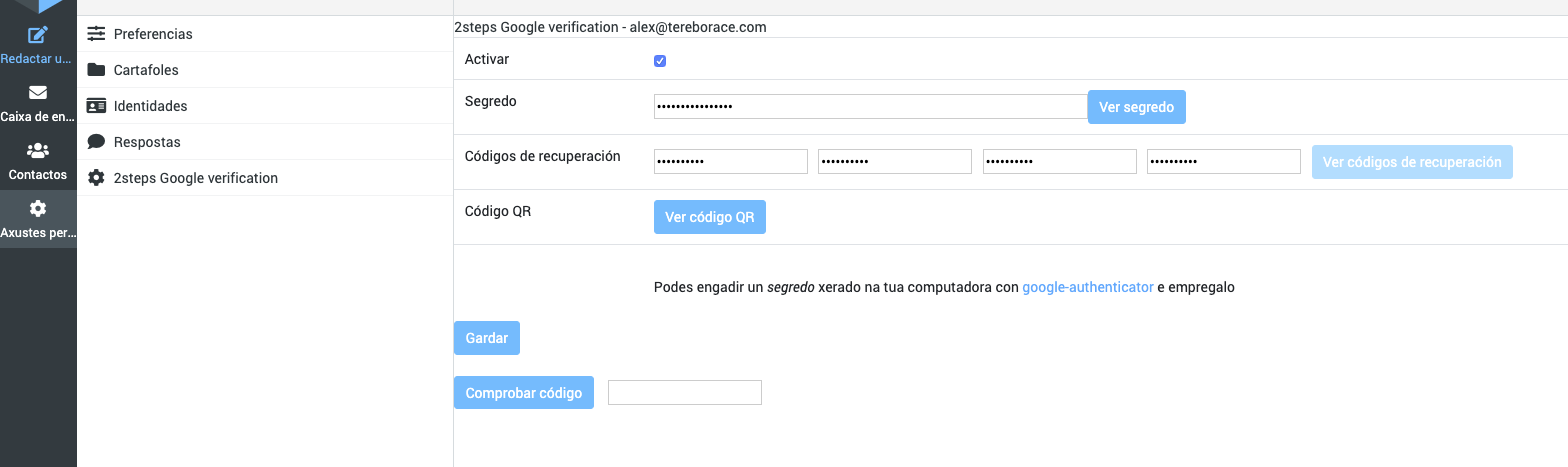
Go to the Settings task and in the "2steps Google verification" menu, click 'Setup all fields (needs Save)'.
The plugin automatically creates the secret for you.
NOTE: plugin must be base32 valid characters ([A-Z][2-7]), see https://github.com/alexandregz/twofactor_gauthenticator/blob/master/PHPGangsta/GoogleAuthenticator.php#L18
From alexandregz#139
To add accounts to the app, you can use the QR-Code (easy-way) or type the secret. After checking the first code click 'Save'.
Also, you can add "Recovery codes" for use one time (they delete when are used). Recovery codes are OPTIONAL, so they can be left blank.
Enrollment Users
If config value force_enrollment_users is true, ALL users needs to login with 2-step method. They receive alert message about that, and they can't skip without save configuration
Samefield
If config value 2step_codes_on_login_form is true, 2-step codes (and recovery) must be sended with password value, append to this, from the login screen: "Normal" codes just following password (passswordCODE), recovery codes after two pipes (passsword||RECOVERYCODE)
Actually only into samefield branch
Codes
Codes have a 2*30 seconds clock tolerance, like by default with Google app (Maybe editable in future versions)
License
MIT, see License
Notes
Tested with RoundCube 0.9.5 and Google app. Also with Roundcube 1.0.4
Remember, sync time it's essential for TOTP: "For this to work, the clocks of the user's device and the server need to be roughly synchronized (the server will typically accept one-time passwords generated from timestamps that differ by ±1 from the client's timestamp)" (from http://en.wikipedia.org/wiki/Time-based_One-time_Password_Algorithm)
Author
Alexandre Espinosa Menor aemenor@gmail.com
Issues
Open issues using github, don't send me emails about that, please -usually Gmail marks messages like SPAM
Testing
- Vagrant: https://github.com/alexandregz/vagrant-twofactor_gauthenticator
- Docker: https://hub.docker.com/r/alexandregz/twofactor_gauthenticator/
Using with Kolab
Add a symlink into the public_html/assets directory
Show explained alexandregz#29 (comment) by https://github.com/d7415
Client implementations
You can use various OTP clients -link by https://github.com/helmo
Logs
Suggested by simon@magrin.com
To log errors with bad codes, change the $_enable_logs variable to true.
The logs are stored to the file HOME_RC/logs/log_errors_2FA.txt -directory must be created
Whitelist
You can define whitelist IPs into config file (see config.inc.php.dist) to automatic login -the plugin don't ask you for code
Uninstall
To deactivate the plugin, you can use two methods:
-
To only one user: restore the user prefs from DB to null (rouncubeDB.users.preferences) -the user plugin options stored there.
-
To all: remove the plugin from config.inc.php/remove the plugin itself
Activate only for specific users
-
Use config.inc.php file (see config.inc.php.dist example file)
-
Modify array users_allowed_2FA with users that you want to use plugin. NOTE: you can use regular expressions
Use with 1.3.x version
Use 1.3.9-version branch
$ git checkout 1.3.9-version
If you download 1.4.x RC version (with elastic skin), use master version normally (thx to tborgans)
Security incident 2022-04-02
Reported by kototilt@haiiro.dev (thx for the report and the PoC script)
I make a little modification on script to not allow to save config without param session generated from a rendered page, to force user to introduce previously 2FA code and navigate across site.
NOTE: Also I check if user have 2FA activated because with only first condition -check SESSION- app kick out me before to activate 2FA.
twofactor_gauthenticator_save()
On function twofactor_gauthenticator_save() I added this code:
// save config function twofactor_gauthenticator_save() { $rcmail = rcmail::get_instance(); // 2022-04-03: Corrected security incidente reported by kototilt@haiiro.dev // "2FA in twofactor_gauthenticator can be bypassed allowing an attacker to disable 2FA or change the TOTP secret." // // Solution: if user don't have session created by any rendered page, we kick out $config_2FA = self::__get2FAconfig(); if(!$_SESSION['twofactor_gauthenticator_2FA_login'] && $config_2FA['activate']) { $this->__exitSession(); }
The idea is to create a session variable from a rendered page, redirected from __goingRoundcubeTask function (redirector to roundcube tasks)
tests with PoC python script
Previously, with security compromised:
alex@vosjod:~/Desktop/report$ ./poc.py Password:xxxxxxxx 1. Fetching login page (http://localhost:8888/roundcubemail-1.4.8) 2. Logging in POST http://localhost:8888/roundcubemail-1.4.8/?_task=login 3. Disabling 2FA POST http://localhost:8888/roundcubemail-1.4.8/?_task=settings&_action=plugin.twofactor_gauthenticator-save POST returned task "settings" 2FA disabled!
Modified code and tested again, not allowed to deactivated/modified without going to a RC task (with 2FA authentication):
alex@vosjod:~/Desktop/report$ ./poc.py Password:xxxxxxxxx 1. Fetching login page (http://localhost:8888/roundcubemail-1.4.8) 2. Logging in POST http://localhost:8888/roundcubemail-1.4.8/?_task=login 3. Disabling 2FA POST http://localhost:8888/roundcubemail-1.4.8/?_task=settings&_action=plugin.twofactor_gauthenticator-save POST returned task "login" Expected "settings" task, something went wrong