jelix / saml-module
module for Jelix, allowing to authenticate against an SAML server.
Installs: 502
Dependents: 0
Suggesters: 0
Security: 0
Stars: 0
Watchers: 1
Forks: 4
Open Issues: 5
Type:jelix-module
pkg:composer/jelix/saml-module
Requires
- php: >=7.4
- onelogin/php-saml: ~4.3.1
- phpseclib/phpseclib: ~3.0.47
- v2.6.0
- dev-master / 2.5.x-dev
- v2.5.0
- v2.4.1
- v2.4.0
- 2.3.x-dev
- v2.3.1
- v2.3.0
- v2.2.5
- v2.2.4
- v2.2.3
- v2.2.2
- v2.2.1
- v2.2.0
- v2.1.5
- v2.1.4
- v2.1.3
- v2.1.2
- v2.1.1
- v2.1.0
- 2.0.x-dev
- v2.0.1
- v2.0.0
- v2.0.0-rc.2
- v2.0.0-rc.1
- v2.0.0-beta.2
- v2.0.0-beta.1
- v2.0.0-alpha.1
- 1.0.x-dev
- v1.0.3
- v1.0.2
- v1.0.1
- v1.0.0
- dev-jelix-auth
- dev-admin-interface
This package is auto-updated.
Last update: 2026-02-16 22:18:30 UTC
README
The "saml" module is a module for Jelix, providing authentication for jAuth against SAML servers.
A "samladmin" module is also provided to configure the "saml" module.
Installation
These modules are for Jelix 1.6.21 and higher. They are compatible with jauth, jauthdb, jauthdb_admin and jcommunity modules.
The saml module uses the onelogin/php-saml library which is installed automatically when using Composer.
To install the SAML modules into Lizmap, read the file README_lizmap.md.
To install the SAML modules into any other application based on Jelix, read the file INSTALL.md.
Authentication
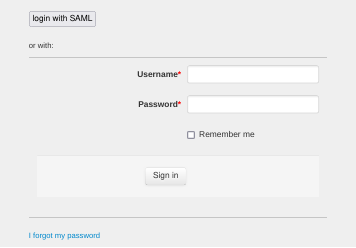
The "saml" module adds a new button on the login form:
You can change the label of the button into the account configuration panel.
Clicking on the button redirect the user to your identity server. The user will then have to authenticate himself if he's not already authenticated, and then he will be redirected back to the application.
Configuration
See the configuration page to discover the samladmin module or to know to configure the saml module without samladmin.