experius / module-csp
Provide a basic Content Security Policy Allowed List and report blocked resources.
Installs: 82 832
Dependents: 0
Suggesters: 0
Security: 0
Stars: 35
Watchers: 5
Forks: 13
Open Issues: 5
Type:magento2-module
pkg:composer/experius/module-csp
- dev-master
- 2.0.3
- 2.0.2
- 2.0.1
- 2.0.0
- 1.8.3
- 1.8.2
- 1.8.1
- 1.8.0
- 1.7.2
- 1.7.1
- 1.7.0
- 1.6.1
- 1.6.0
- 1.5.0
- 1.4.0
- 1.3.7
- 1.3.6
- 1.3.5
- 1.3.4
- 1.3.3
- 1.3.2
- 1.3.1
- 1.3.0
- 1.2.30
- 1.2.29
- 1.2.28
- 1.2.27
- 1.2.16
- 1.2.15
- 1.2.14
- 1.2.13
- 1.2.12
- 1.2.11
- 1.2.10
- 1.2.9
- 1.2.8
- 1.2.7
- 1.2.6
- 1.2.5
- 1.2.4
- 1.2.3
- 1.2.2
- 1.2.1
- 1.2.0
- 1.1.1
- 1.1.0
- 1.0.1
- 1.0.0
- dev-feature/SPC-3021
- dev-feature/SBAS-1452
- dev-feature/SFIN-60_adminhtml-whitelisting
- dev-bugfix/DOBO-262
- dev-feature/ARCI-143_introduce-on-off-switch
- dev-feature/DLTSM2-617
- dev-feature/expand-csp-whitelist
- dev-additional-defaults-1
This package is auto-updated.
Last update: 2026-02-16 17:29:35 UTC
README
experius/module-csp
- Installation
- Main Functionalities
- Basic allowed list
- Content Security Policy Reporting & whitelisting
- Add a resource to the allowed list permanently
Installation
In production please use the --keep-generated option
- Install the module composer by running
composer require experius/module-csp - enable the module by running
php bin/magento module:enable Experius_Csp - apply database updates by running
php bin/magento setup:upgrade - Flush the cache by running
php bin/magento cache:flush
Main Functionalities
Provide a basic Content Security Policy allowed-list (whitelist) and when the Resource should be blocked it will automatically be reported within the Experius CSP Report Table (experius_csp_report).
When there is a report of a blocked directive is found, an error message will be show in the admin to notify the developer/client.
These reports can be whitelisted for directive which allow this. See "Content Security Policy Reporting & whitelisting" below for an example and more details.
IMPORTANT: Content Security Policy Report Only Mode
In the upcoming Magento 2.4 Release then the Content Security Policy Report Only Mode then will be disabled and it will validate strict.
The report-to has been disabled in this version because it is not working properly. See: \Experius\Csp\Plugin\Magento\Framework\App\Response\HttpInterface::beforeSetHeader
Basic allowed list
Currently this module contains a basic whitelist of considerd "safe" sources.
A few examples:
- Google Fonts
- Google Maps
- Dotdigital / Dotmailer Chat
- Buckaroo
- etc.
For a full list for each directive, please check the following file:
etc/csp_whitelist.xml
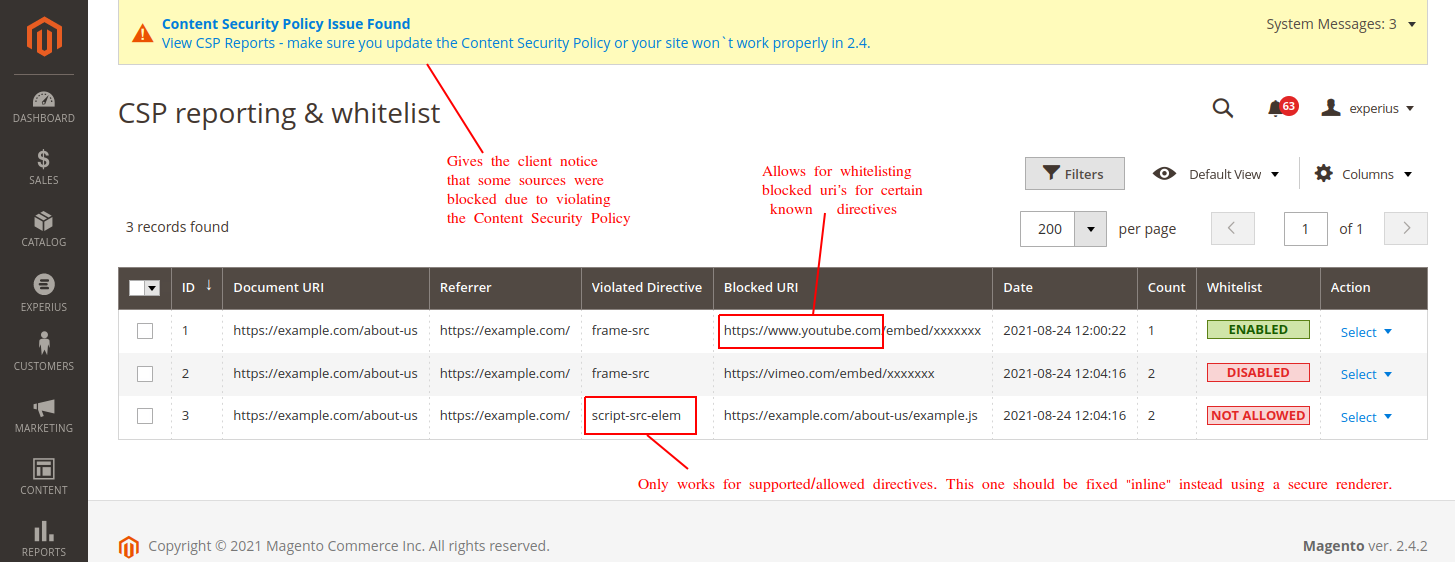
Content Security Policy Reporting & whitelisting
In the Magento Admin you can view the reports which are created.
System > Tools > CSP reporting & whitelist
To avoid clutter a counter is introduced, which prevents the table from growing in size excessively with many pageviews. This is grouped by "violated_directive", "blocked_uri" and "document_uri".
@TODO: [Nice to have] consider letting louse "document_uri", since whitelist is applied across the entire Magento installation (globally).
Add a resource to the allowed list permanently
Based on the reports you can easily add a csp_whitelist.xml file within your own modules and when you are done just delete the record because it no longer is relevant. More information about how this xml file works you can find here:
https://devdocs.magento.com/guides/v2.3/extension-dev-guide/security/content-security-policies.html
For example Report:
- document_uri: https://example.com/
- referer:https://example.com/
- violated_directive: img-src
- original_policy: font-src fonts.googleapis.com fonts.gstatic.com https://www.gstatic.com https://fonts.gstatic.com 'self' 'unsafe-inline'; form-action 'self' 'unsafe-inline'; frame-ancestors 'self' 'unsafe-inline'; frame-src cdn.dnky.co youtube.com www.youtube.com https:/
- blocked_uri: https://maps.gstatic.com/mapfiles/openhand_8_8.cur
- date: 2020-06-25 16:42:23
Fix:
# app/code/Custom/Csp/etc/csp_whitelist
<?xml version="1.0"?>
<csp_whitelist xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:noNamespaceSchemaLocation="urn:magento:module:Magento_Csp:etc/csp_whitelist.xsd">
<policies>
<policy id="img-src">
<values>
<value id="gstatic" type="host">*.gstatic.com</value>
</values>
</policy>
</policies>
</csp_whitelist>