causal / fal-protect
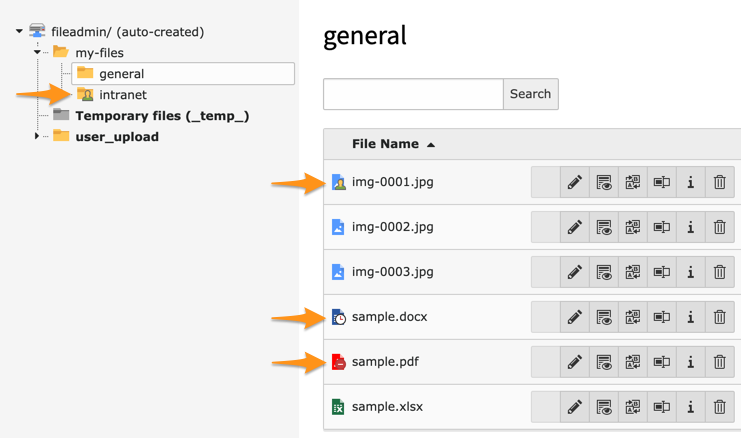
Protect everything within /fileadmin/ based on associated folder and file restrictions (visibility, user groups and dates of publication).
Fund package maintenance!
xperseguers
www.paypal.me/xperseguers/10
Installs: 66 905
Dependents: 0
Suggesters: 2
Security: 0
Stars: 12
Watchers: 2
Forks: 11
Open Issues: 5
Type:typo3-cms-extension
pkg:composer/causal/fal-protect
Requires
- php: >=7.4.1 <=7.4.99 || >=8.0.0 <=8.4.99
- typo3/cms-core: ^11 || ^12 || ^13
This package is auto-updated.
Last update: 2026-02-12 13:28:06 UTC
README
This extension protects everything within /fileadmin/ or other relative storages based on associated folder and file
restrictions (visibility, user groups and dates of publication):
Unlike other similar extensions securing the File Abstraction Layer (FAL) of TYPO3, this extension aims at making it straightforward to block direct access to your sensitive assets.
No need to configure anything, just install and enable as usual, block direct access at the server level (Apache/Nginx see below) and... that's it!
Our motto? KISS!
Installation (Apache)
Edit file .htaccess to read:
RewriteCond %{REQUEST_URI} !/fileadmin/_processed_/.*$
RewriteRule ^fileadmin/.*$ %{ENV:CWD}index.php [QSA,L]
BEWARE: Be sure to add this rule before any other related rule.
Installation (Nginx)
Edit your server block to read:
location / {
rewrite ^/fileadmin/(?!(_processed_/)) /index.php last;
# snip
}
or, if that better fits your setup, like that:
location ~ /fileadmin/(?!(_processed_/)) {
rewrite ^(.+)$ /index.php last;
}
Why 404 instead of 403 by default?
In case you try to access a restricted file and do not have the right to do so, the logical HTTP status code to use
should be either a 403 Forbidden (or possibly a 401 Unauthorized) but by doing so, you make it clear for a
malicious user that the resource exists but is not accessible.
We prefer, by default, to issue a 404 Not Found but you can freely choose to issue a 403 Forbidden in the extension
settings. This is particularly useful if you plan to redirect to a login page when a user tries to access a restricted
resource.
Complete documentation
A more complete documentation can be found on https://docs.typo3.org/p/causal/fal-protect/main/en-us/.